Have you ever received a phone call from a familiar company or institution that didn’t seem quite right? Maybe the conversation seemed odd, or the voice at the other end was a recording. In these cases, you should always trust your instincts. You might indeed have been the target of a phone scam or vishing.
In 2022, vishing hit 1 in 3 Americans. In the same year, vishing attacks increased by 550%, costing their victims 68.4 million dollars (source: Techreport). Here is how to recognize vishing and protect yourself.
What is vishing?
 Vishing, also known as “voice phishing,” is a social engineering attack that manipulates individuals into divulging sensitive information or performing actions over the phone.
Vishing, also known as “voice phishing,” is a social engineering attack that manipulates individuals into divulging sensitive information or performing actions over the phone.
It involves fraudulent phone calls, recorded messages, or voicemails that appear to come from legitimate sources, such as financial institutions, government agencies, or reputable organizations.
Vishing attacks try to obtain personal or financial information, such as passwords, social security numbers, or credit card details. The attacker will then use them for fraudulent purposes.
Vishing attacks rely on tactics to trick victims into providing the requested information or taking actions that benefit the attacker.
Who are the victims of vishing?
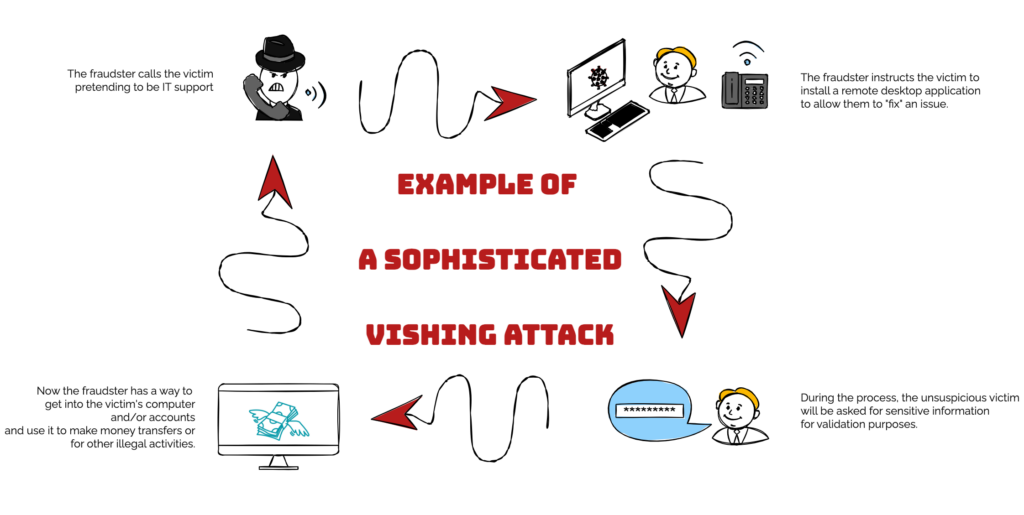
Vishing attacks exploit people’s vulnerabilities, lack of knowledge, or experience. Typical targets are older people, people without knowledge of phone fraud, or new immigrants. However, anybody could be a target, as these attacks can be quite sophisticated and difficult to detect.
Vishing attacks might not always target individuals; businesses are also targets. In these cases, vishing attacks target employees with higher access to the company’s systems or financial resources, such as IT administrators, accountants, or executives.
How vishing attacks exploit victims

Vishing attacks leverage the inherent trust associated with phone communications to deceive victims. Over the phone, cybercriminals will create convincing scenarios that trick individuals into divulging sensitive information or performing actions that compromise their security.
Fraudsters typically impersonate banks, tech support, investment or loan experts, medicare representatives, telemarketing, or the Government.
These attacks are often “low tech”. However, scammers can leverage VoIP (Voice over IP) telephony, which allows them to activate local phone numbers, use them, and decommission them with just a few clicks.
More advanced scams might use recorded messages or spoofing (they can make it look like they’re calling from a legitimate number even if they’re not).
Tactics employed in vishing
Vishing focuses on manipulating human psychology more than technology. Phone scammers typically use the following tactics to succeed:
URGENCY AND PRESSURE
 Vishing attacks often try to manipulate victims into taking immediate action without critically assessing the situation. Cybercriminals create a sense of urgency by fabricating scenarios that trigger fear or panic, compelling victims to act hastily to avoid perceived consequences. For example, attackers may claim that the victim’s bank account was compromised and that they need to take urgent steps to prevent unauthorized access or financial loss. By eliciting a quick response, they increase the likelihood of compliance with their demands.
Vishing attacks often try to manipulate victims into taking immediate action without critically assessing the situation. Cybercriminals create a sense of urgency by fabricating scenarios that trigger fear or panic, compelling victims to act hastily to avoid perceived consequences. For example, attackers may claim that the victim’s bank account was compromised and that they need to take urgent steps to prevent unauthorized access or financial loss. By eliciting a quick response, they increase the likelihood of compliance with their demands.
REQUESTS FOR SENSITIVE INFORMATION

One of the primary objectives of vishing attacks is to obtain sensitive information from victims, such as passwords, social security numbers, or financial details, which can be used for fraud. By preying on victims’ trust and exploiting their willingness to comply with perceived authority figures, vishing attackers aim to gather valuable data that can be exploited for financial gain or identity theft.
CALLER ID SPOOFING AND IMPERSONATION OF LEGITIMATE ENTITIES
 Caller ID spoofing is a common technique used in vishing attacks to deceive victims into believing that the incoming call is from a legitimate source. By manipulating caller ID information to display a trusted entity’s name or phone number, cybercriminals create a false sense of familiarity and credibility, increasing the likelihood that victims will answer the call and engage in conversation. Additionally, vishing perpetrators may impersonate legitimate entities such as banks, government agencies, or service providers, adopting convincing personas to gain victims’ trust and elicit sensitive information.
Caller ID spoofing is a common technique used in vishing attacks to deceive victims into believing that the incoming call is from a legitimate source. By manipulating caller ID information to display a trusted entity’s name or phone number, cybercriminals create a false sense of familiarity and credibility, increasing the likelihood that victims will answer the call and engage in conversation. Additionally, vishing perpetrators may impersonate legitimate entities such as banks, government agencies, or service providers, adopting convincing personas to gain victims’ trust and elicit sensitive information.
how to recognize a vishing attempt
 Besides the common tactics used in vishing attempts, you can watch out for the following red flags whenever you receive a call:
Besides the common tactics used in vishing attempts, you can watch out for the following red flags whenever you receive a call:
Mismatched Caller ID Information: If the caller ID information displayed does not match the expected source of the call, it could be a sign of spoofing. For example, a call from a familiar organization or individual may be spoofed if the caller ID shows a different name or number.
Unsolicited Calls: Spoofed calls are often associated with unsolicited or unexpected calls, especially those that pressure you to provide personal or financial information. Be cautious of calls from unknown numbers that seem suspicious or out of the blue.
Robocalls or Automated Messages: Robocallers or automated systems generate many spoofed calls. If you receive a prerecorded message or automated voice prompting you to take action or provide information, it’s highly suspicious.
No Callback Ability: Some spoofed numbers may not allow you to call back or reach a legitimate contact. If you attempt to return the call and encounter issues such as disconnected lines or automated messages, it may be a temporary or a spoofed number.
Caller Behavior: Pay attention to the behavior of the caller. Spoofed callers may exhibit aggressive behavior or won’t answer your questions, going back to their script to pressure you into taking some kind of action or giving them some confidential information. Also pay attention to the way they speak: a foreign accent and poor grammar might indicate that the call is coming from abroad.
Unusual Number Patterns: Look for unusual number patterns or discrepancies in the caller ID information, such as missing or extra digits, unfamiliar area codes, or numbers that do not conform to standard formatting.
Verification with the Legitimate Source: If you receive a call from a known organization or individual but they won’t provide their names and contact information for validation, the call is likely to be a scam.
How to protect yourself from vishing
 Here are some general tips to prevent phone scams:
Here are some general tips to prevent phone scams:
- Never provide personal or financial information over the phone unless you know the caller’s identity. Most institutions or Government bodies will not ask you for sensitive information over the phone.
- Utilize call-blocking features on smartphones to filter out spam calls.
- Register your phone number on the “Do Not Call” lists. You can do that from Canada’s National Do Not Call List, or the US National Do Not Call Registry.
- Be cautious of unsolicited calls and verify the legitimacy of callers through independent means.
- Report suspicious calls to relevant authorities or telecommunications providers. In Canada, contact the Canadian Anti-Fraud Center or, in the United States, file a complaint with the FBI’s IC3 (Internet Crime Complaint Center).
- Educate family members and colleagues about vishing risks and prevention measures.
Remember that you can always back out of a situation that makes you feel uncomfortable. If you suspect the call might not be legitimate, politely terminate the call and ask for the caller’s contact information so that the conversation can resume later. This will allow you to validate that they are who they are and put your mind at ease.
Now that you know how to recognize vishing, take the steps to stay safe!
DID YOU KNOW?
 At Negative PID, we offer services to help you validate phone numbers and email addresses. Our email or phone validation checks for an email address or phone number’s reputation online. The results indicate if an email address or phone number has been flagged or reported for unusual or suspect activities often associated with spam, spoofing, fraud, or abuse.
At Negative PID, we offer services to help you validate phone numbers and email addresses. Our email or phone validation checks for an email address or phone number’s reputation online. The results indicate if an email address or phone number has been flagged or reported for unusual or suspect activities often associated with spam, spoofing, fraud, or abuse.
If you don’t know how to report a case of vishing, we can help you do that.




