In recent years, cybersecurity topics have become increasingly familiar to the public. Movies and TV shows with hackers as central characters have also popularized the Dark Web and made it a familiar concept to many. However, what do you know about the Dark Web? Can you differentiate fiction from reality?
In this cybersecurity awareness month, let’s deep dive into one of the most mysterious and controversial online places there is.
What is the Dark Web?
 The dark web is a part of the internet that is not indexed by traditional search engines and requires specific software, such as Tor (The Onion Router), to access. While it is often associated with illegal activities, the dark web also serves legitimate purposes, such as protecting the privacy of journalists, activists, and whistleblowers in oppressive environments.
The dark web is a part of the internet that is not indexed by traditional search engines and requires specific software, such as Tor (The Onion Router), to access. While it is often associated with illegal activities, the dark web also serves legitimate purposes, such as protecting the privacy of journalists, activists, and whistleblowers in oppressive environments.
The first thing you should understand about the Dark Web is that it is a layer of the World Wide Web:
- The Surface Web is the visible, publicly accessible part of the Internet. Websites indexed by search engines like Google or Bing fall under this category, making up around 4-5% of the total internet.
- The Deep Web includes data not indexed by search engines, such as medical records, academic databases, and subscription-based content.
- The Dark Web is a subset of the deep web; the dark web is intentionally hidden and only accessible using special anonymizing tools like Tor or I2P (Invisible Internet Project).
How does the Dark Web work?
The dark web uses encryption techniques to hide users’ identities and locations. For example, Tor anonymizes users by routing traffic through multiple volunteer-operated servers, making tracing difficult. Websites on the dark web often have .onion URLs, which cannot be accessed by conventional browsers but are accessible through Tor. These URLs are randomly generated strings, providing a layer of obscurity. Unlike the traditional web, the dark web lacks centralized hosting services. Websites are hosted on individual servers, making tracking difficult.
What is the Dark web used for?
The Dark Web is used for illicit and legitimate purposes alike. Among illegal activities, there are:
- Black markets: The dark web is notorious for hosting black markets like Silk Road (now shut down), where illegal goods such as drugs, weapons, and counterfeit documents are sold.
- Hacking services: It’s a hub for criminal hackers offering services like selling exploits, ransomware, malware, and stolen data.
- Human trafficking: Some areas of the dark web are used for heinous activities like human trafficking and illegal pornography.
- Illegal finances: Cryptocurrencies like Bitcoin and Monero are popular due to their perceived anonymity and are often used for money laundering or buying illegal products.
Among its legitimate uses are:
- Privacy advocacy: For people in oppressive regimes, journalists, and activists, the dark web offers a way to communicate without fear of surveillance or censorship.
- Whistleblowing: Platforms like SecureDrop provide a safe environment for whistleblowers to anonymize information.
- Research: Cybersecurity professionals and law enforcement agencies often explore the dark web to monitor criminal activity and gather intelligence.
Is the Dark Web safe?
Simply browsing the dark web is not illegal in many countries, but accessing or engaging with illegal content is. Many users inadvertently expose themselves to law enforcement. That said, if you decide to browse the Dark Web, you should do so at your own risk: the dark web is rife with malicious links, malware, and phishing attacks that can compromise a user’s device or data. Fraud is rampant, with users often scammed out of money for fake services or products. The lack of regulation makes recourse difficult. Finally, exposure to the dark web’s disturbing content, such as violent imagery or exploitation, can have a profound psychological toll.
TOR vs I2P
The most popular way to access the dark web is Tor (The Onion Router). Tor routes traffic through multiple nodes (or relays), providing anonymity. Another anonymizing network, less popular than Tor, is I2P (Invisible Internet Project). I2P emphasizes peer-to-peer communication, with a different focus on how anonymity is preserved.
| TOR | I2P |
|---|---|
| Tor was primarily designed to anonymize web browsing and facilitate access to both the surface web and the dark web. | I2P was built for peer-to-peer (P2P) communication, with a strong focus on anonymizing services within the network itself rather than external web browsing. |
| Tor directs user traffic through a series of volunteer-operated servers (called relays or nodes), making it difficult to trace the user's original IP address. | I2P routes traffic over a decentralized, distributed network. Unlike Tor, I2P does not rely on centralized directories for routing information. |
| The traffic is layered in encryption and passed through multiple relays, each decrypting one layer (hence the "onion" metaphor). Only the last relay (the exit node) accesses the destination, but it cannot trace back the user’s origin. | I2P uses a method called garlic routing, where multiple messages are bundled together into a single "clove" to improve anonymity and reduce traffic analysis. |
| Use Cases: Anonymous web browsing, access to .onion sites (dark web websites), circumventing censorship and surveillance in oppressive regimes. | Use Cases: Anonymized messaging and P2P file sharing, hosting internal sites ("eepsites", or I2P websites), running services (like chat and file transfer) within I2P itself. |
 Tor is more widely known, with extensive documentation, resources, and community support. Many large organizations, including human rights groups, privacy advocates, and journalists, use Tor to access restricted information and communicate securely. Furthermore, Tor can be used to browse both the clear web and the dark web (.onion sites). This dual capability makes it more versatile for general use.
Tor is more widely known, with extensive documentation, resources, and community support. Many large organizations, including human rights groups, privacy advocates, and journalists, use Tor to access restricted information and communicate securely. Furthermore, Tor can be used to browse both the clear web and the dark web (.onion sites). This dual capability makes it more versatile for general use.
On the other hand, I2P provides better internal network anonymity. Since it’s designed to operate mainly within its network, there’s no exit point vulnerability like in Tor (where exit nodes can be monitored). All communication within I2P is encrypted end-to-end, even between internal services. Moreover, I2P excels in applications like anonymous file sharing (e.g., BitTorrent), messaging, and hosting decentralized services. The network is decentralized, and garlic routing offers better resistance to traffic analysis than Tor’s onion routing in specific use cases. Finally, I2P is typically faster than Tor for internal network communications, as it’s optimized for low-latency activities like chatting, P2P transfers, and running services on the I2P network.
Marketplaces and forums in the Dark Web
Some of the most popular features of the Dark Web are marketplaces where you can find illegally sold goods and services.
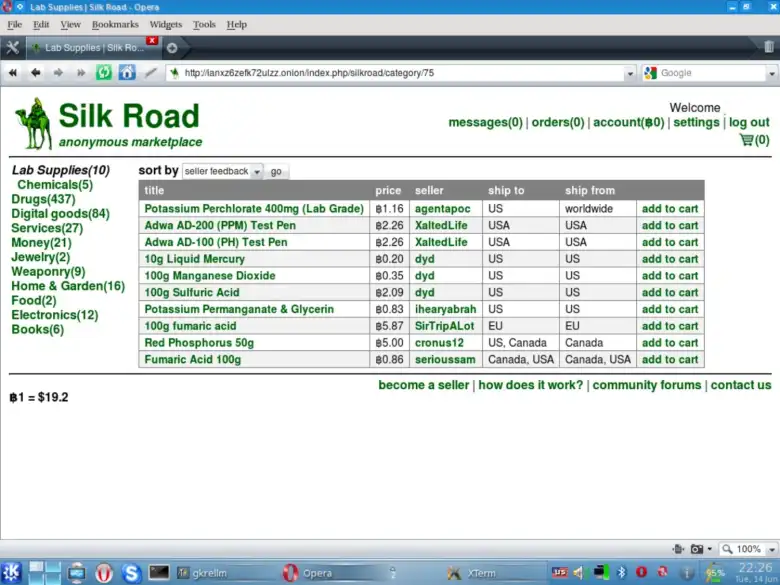 For example, the Silk Road was one of the earliest and most famous dark web marketplaces known for selling drugs, weapons, and illegal services. It was shut down by the FBI in 2013. AlphaBay & Hansa were two of the largest markets post-Silk Road. They were shut down in 2017 by a coordinated law enforcement operation. AlphaBay offered illegal drugs, weapons, and hacking tools. One of the more recent marketplaces, Empire Market, operated until its sudden disappearance. It is considered an exit scam, where operators shut down and disappear with user funds.
For example, the Silk Road was one of the earliest and most famous dark web marketplaces known for selling drugs, weapons, and illegal services. It was shut down by the FBI in 2013. AlphaBay & Hansa were two of the largest markets post-Silk Road. They were shut down in 2017 by a coordinated law enforcement operation. AlphaBay offered illegal drugs, weapons, and hacking tools. One of the more recent marketplaces, Empire Market, operated until its sudden disappearance. It is considered an exit scam, where operators shut down and disappear with user funds.
Very popular on the dark web are also forums serving as communities for discussing illegal activities like hacking, carding (credit card fraud), drug trade, and other forms of criminal behaviour. These forums often require registration and vetting to gain access, and new users may be asked to prove their legitimacy by completing tasks.
Dark Web and Cryptocurrencies
Cryptocurrencies, particularly Bitcoin and Monero, are commonly used on the dark web due to their anonymity features. Bitcoin, while traceable in some cases, is widely accepted, while Monero is favoured for its stronger privacy protections. Cryptocurrencies have enabled various financial activities, including the purchasing of illegal goods, untraceable transactions, and laundering money. This is why Cryptocurrencies have found a large use in the Dark Web.
The Law Enforcement in the Dark Web
 One of the most frequent questions about the dark web is why law enforcement doesn’t do anything to shut down illegal websites. The answer is complicated, but it could be summarized as a matter of jurisdiction. Tracing dark web websites on the dark web to a specific country is complex, and unless there is an incident where a victim or a crime can be located, intervention cannot be initiated.
One of the most frequent questions about the dark web is why law enforcement doesn’t do anything to shut down illegal websites. The answer is complicated, but it could be summarized as a matter of jurisdiction. Tracing dark web websites on the dark web to a specific country is complex, and unless there is an incident where a victim or a crime can be located, intervention cannot be initiated.
However, law enforcement is present on the dark web, and whenever possible, they take action with large operations. For example, in Operation Onymous in 2014, a coordinated global law enforcement effort led to the seizure of several dark web marketplaces, including Silk Road 2.0. This operation highlighted law enforcement’s capability to infiltrate dark web operations.
Law enforcement agencies use a variety of tactics to track criminals on the dark web, such as honeypots (fake dark web services designed to lure and track users) or exploiting vulnerabilities in Tor or user errors. However, The anonymity of the dark web makes it hard for law enforcement to shut down illegal activities entirely. When one market is taken down, another often takes its place.
Ethical implications of the Dark Web
The dark web presents a tension between freedom of speech, privacy, and the ability to evade law enforcement. While it offers a lifeline for those needing anonymity, it also fosters a haven for illegal activity. The dark web also poses regulatory challenges that are hard to circumnavigate: governments worldwide are grappling with regulating the dark web, balancing protecting privacy and addressing criminal use.
The dark web continues to evolve, with increasingly sophisticated technologies for both criminal activities and law enforcement tactics. The continued development of blockchain technologies, better anonymizing tools, and AI-driven security tools are shaping its future, as law enforcement and criminals play an ongoing game of cat and mouse.
The shift from the dark web to social media

Lately, young users have been shifting from the dark web to mainstream platforms like Discord for activities previously associated with the dark net. This represents a broader trend in how certain illicit or risky behaviours evolve in the digital landscape. Several factors contribute to this migration, and the implications are complex, blending convenience, anonymity, and a sense of community, often bypassing the need for more specialized, hard-to-access dark web environments.
Among the main reasons for the shift are:
- Ease of access: Accessing the dark web requires technical know-how, such as configuring tools like Tor or I2P and knowing where to find hidden services. Young users often lack the technical proficiency to navigate this ecosystem securely. Platforms like Discord are much easier to use. Creating an account and joining a server takes minutes, providing an instant and often unmonitored environment for users to engage in various activities.
- Anonymity and perceived safety: Discord allows users to operate under pseudonyms and use private or encrypted communication (direct messages, private servers), giving a sense of anonymity similar to the dark web but without the complicated setup. Additionally, many young users perceive platforms like Discord as safer environments because they are more familiar, easily accessible, and less dangerous than the dark web. This sense of security can lead to risky behaviours, as they may underestimate the possibility of law enforcement monitoring or being exposed by peers.
Discord and other platforms like Telegram have evolved to include spaces where illicit activities, such as drug dealing, hacking, and sharing explicit content, are normalized, particularly in private servers. These communities often form subcultures that glamorize such behavior. Although Discord has community guidelines, moderation on these platforms can be inconsistent. Private servers, which are often invite-only, are difficult for moderators and law enforcement to monitor unless specifically reported. This makes it easier for groups to share illicit content or engage in illegal activities under the radar.
Social media are now at the forefront of this new wave of digital underground activities, and the challenge lies in effectively moderating and educating users on the risks.
Finding a balance
The dark web is a complex, multifaceted realm that serves as a refuge for privacy advocates and a den for criminal activity. While it offers essential services for those needing anonymity, the risks of legal exposure, malware, and psychological harm are considerable. At the same time, online crime and illegal activities are migrating to more diffused and easy-to-access platforms for younger users.
Law enforcement and ethical hackers are constantly working to find a balance in understanding and managing these challenges.




