In our previous article, we examined the best practices for preventing application-level hijacking attacks. We’ll now discuss using secure protocols to implement security measures for network-level session hijacking threats.
What is network-level session hijacking?
 Network-level session hijacking occurs when an unauthorized user intercepts and takes over a session between a client (in this case, a browser) and a server.
Network-level session hijacking occurs when an unauthorized user intercepts and takes over a session between a client (in this case, a browser) and a server.
This allows them to access sensitive information or potentially perform malicious actions.
Network-level hijacking techniques
The most popular network hijacking techniques target the vulnerabilities of protocols commonly used by web applications to communicate information with the server.
These cyber-attacks are relatively easy to execute and highly effective. Here are the most common:
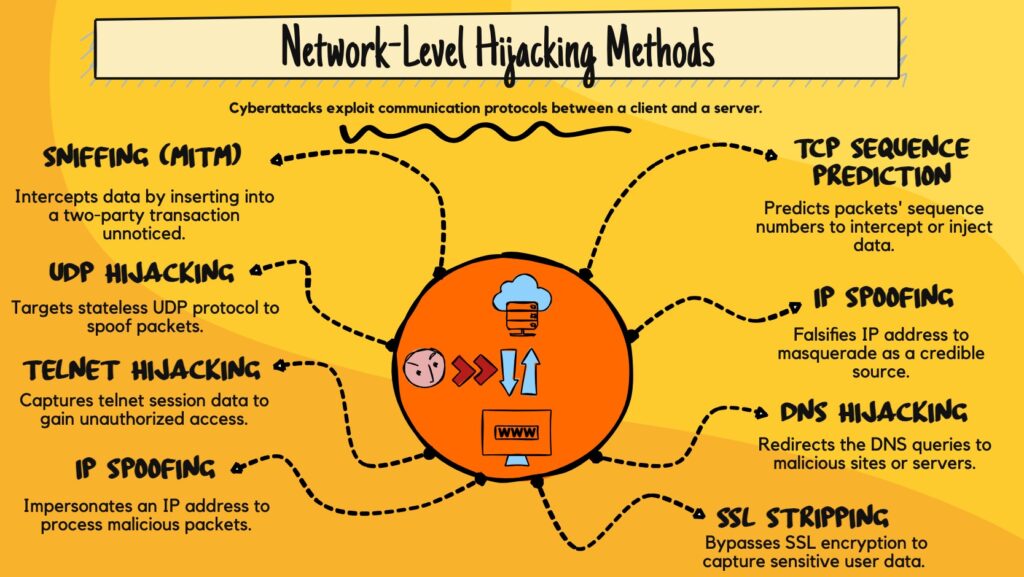
- Sniffing (MITM): In a Man-in-the-Middle (MITM) attack, an attacker intercepts and monitors communication between the client and the server without their knowledge. Capturing data packets transmitted over a network, an attacker can view sensitive information such as login credentials, financial details, or personal data.
- TCP sequence prediction: Attackers use this technique to hijack TCP connections by guessing the sequence numbers of TCP packets. This enables them to inject malicious packets into the communication stream, impersonate legitimate users, or disrupt the connection.
- UDP session hijacking: Unlike TCP, UDP (User Datagram Protocol) UDP is connectionless, making it vulnerable to hijacking as there is no inherent session establishment or validation mechanism.
- IP spoofing: By falsifying the source IP address in packet headers, the attacker can deceive network devices into accepting and processing malicious packets, leading to various attacks, including DDoS (Distributed Denial of Service) attacks or session hijacking.
- Telnet session hijacking: Telnet transmits data in plain text. Attackers interjecting Telnet communications can easily capture and manipulate sensitive information, including login credentials, commands, and data exchanged during the session.
- DNS session hijacking: Attackers can manipulate DNS (Domain Name System) queries or responses to redirect users to malicious websites or servers. This enables various types of attacks, including phishing or malware distribution.
- ARP poisoning: ARP (Address Resolution Protocol) poisoning is a network attack where an attacker falsifies ARP messages to associate their MAC (physical) address with the IP address of a legitimate network device. The attacker can intercept and redirect traffic intended for other hosts, facilitating eavesdropping or MITM attacks.
- SSL Stripping: SSL stripping is an attack where an attacker downgrades HTTPS connections to unencrypted HTTP connections, allowing them to intercept and view sensitive information transmitted between a client and a server.
To mitigate the risk of network-level session hijacking, developers must implement robust security measures, such as Transport Layer Security (TLS) and secure protocols.
Best practices for implementing TLS
 Implementing Transport Layer Security (TLS) is a fundamental step for protecting network traffic against Man-In-The-Middle (MITM) attacks. This happens by encrypting the communication between clients and servers.
Implementing Transport Layer Security (TLS) is a fundamental step for protecting network traffic against Man-In-The-Middle (MITM) attacks. This happens by encrypting the communication between clients and servers.
- Use HTTPS instead of HTTP: HTTP (Hypertext Transfer Protocol) transmits data in plain text, making it vulnerable to interception. In contrast, HTTPS (HTTP Secure) encrypts data using TLS, ensuring confidentiality and integrity. Developers should enforce HTTPS for all web applications to safeguard sensitive information transmitted over the network.
- Employ FTPs instead of FTP: FTP (File Transfer Protocol) sends credentials and data in clear text, posing a significant security risk. FTPs (FTP Secure) uses TLS encryption to protect data during transmission, mitigating the risk of eavesdropping and unauthorized access.
- Implement SSL/TLS for IMAP and POP: Internet Message Access Protocol (IMAP) and Post Office Protocol (POP) are commonly used for email retrieval but can expose credentials and emails to interception. Secure IMAP (IMAPS) and Secure POP (POPS) leverage SSL/TLS encryption to secure email communication, preventing session hijacking and unauthorized access to email accounts.
Best practices for implementing secure protocols
 In addition to TLS, developers should adopt secure protocols to enhance network security:
In addition to TLS, developers should adopt secure protocols to enhance network security:
- Replace Telnet with SSH: Telnet is a legacy protocol that transmits data, including login credentials, in plain text, making it susceptible to interception. Secure Shell (SSH) provides encrypted communication and remote access, making it a safe alternative to Telnet for command-line server access.
- Use SFTP instead of FTP: Similar to FTP, the Secure File Transfer Protocol (SFTP) allows secure file transfers over a network. Unlike FTP, SFTP encrypts commands and data, reducing the risk of unauthorized access and interception.
- Use a VPN for secure access: Virtual Private Network (VPN) technology establishes a secure, encrypted connection over the internet, enabling users to access critical infrastructure securely. Developers should use VPNs to protect data from interception and session hijacking when accessing sensitive resources or utilizing open networks.
Preventing network-level session hijacking requires a multi-layered approach, encompassing secure protocols and encryption mechanisms. By implementing TLS, employing secure protocols such as HTTPS, FTPs, SSH, and SFTP, and utilizing VPNs, web app developers can effectively mitigate the risk of session hijacking and safeguard the integrity and confidentiality of their user’s data.
The following article will explore how to design an overall secure architecture for web applications.




