A robust architecture is the foundation of a secure web application, and adhering to best practices is essential to mitigate risks effectively. In our previous articles, we have explored how to prevent application-level and network-level session hijacking attacks. Let’s now delve into design implementations for crafting a secure architecture for web applications.
Changing the way you design web apps
Designing a secure architecture for web applications involves combining best practices and robust security measures.
In the traditional web app development lifecycle model, security concerns are addressed only at the end of the cycle.
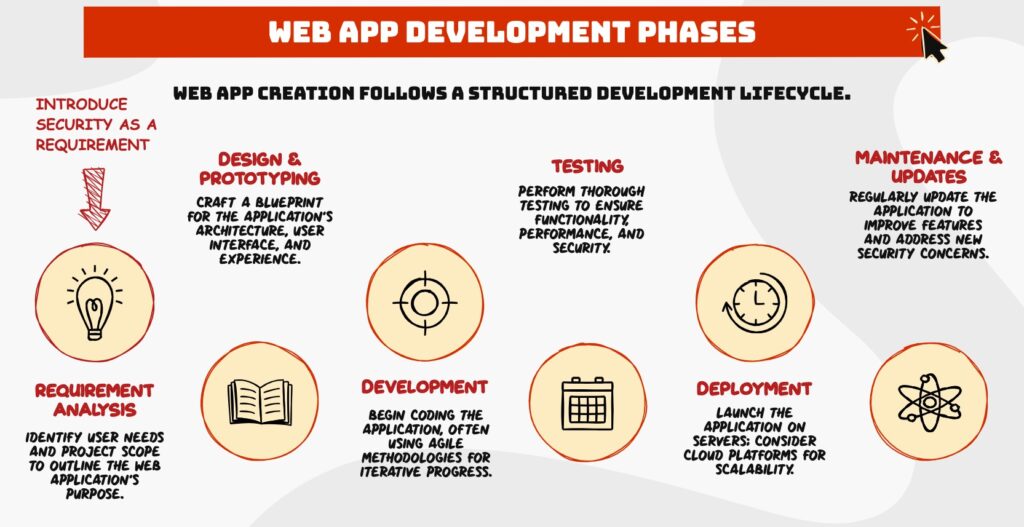
By integrating security into the application design since the first phases of the project, developers can significantly enhance the security posture of their web applications, safeguarding them against a myriad of potential threats.
Best practices for secure architecture design implementations
 Generate new authentication tokens: Whenever possible, generate new ones for sensitive actions instead of relying solely on session IDs. This approach enhances security by reducing the risk of session hijacking.
Generate new authentication tokens: Whenever possible, generate new ones for sensitive actions instead of relying solely on session IDs. This approach enhances security by reducing the risk of session hijacking.- Use built-in session management implementations: Frameworks such as J2EE, PHP, and ASP.NET offer built-in session management implementations. Leveraging these frameworks ensures robust session handling mechanisms, reducing the likelihood of security loopholes.
- Employ secure session ID exchange mechanisms: Ensure that the server only accepts specific types of inputs for session ID exchange. By validating and restricting session ID exchange channels, you can thwart attackers attempting to exploit alternative channels.
- Beware of HTML Web Storage API: Avoid storing sensitive data persistently in browser data stores, such as those provided by the HTML5 Web Storage API. Storing sensitive information in such repositories can lead to information leakage, particularly on shared systems.
- Sanitize session IDs: Sanitize session IDs effectively, treating them as you would any other input. This practice helps prevent injection attacks and ensures the integrity of session management.
- Differentiate cookies: When employing multiple cookies, assign distinct names to each. Additionally, validate both cookies to ensure they are valid within the defined scopes, thereby fortifying your application against potential exploits.
- Re-authenticate users for critical actions: Prioritize user re-authentication before permitting essential actions within the application. This additional layer of authentication adds an extra barrier against unauthorized access to sensitive functionalities.
- Bind session ID with other parameters: To mitigate the risk of session hijacking, bind session IDs with additional parameters such as IP addresses, user agents, or other identifying factors. This makes it more challenging for attackers to hijack sessions successfully.
Remember, security is not a one-time endeavour but an ongoing commitment to staying vigilant and proactive in the face of evolving cyber threats.
What's In it for you?
 Implementing a secure architecture for web applications offers several advantages for developers and companies alike.
Implementing a secure architecture for web applications offers several advantages for developers and companies alike.
- Reputation: Firstly, it enhances the reputation of the developer or company by demonstrating a commitment to safeguarding user data and maintaining trustworthiness. With data breaches and cyber-attacks becoming increasingly prevalent, users are more inclined to engage with applications that prioritize security.
- Customer retention: This can result in improved customer retention and acquisition, ultimately leading to business growth.
- Decreased remediation costs: Additionally, investing in robust security measures upfront can lead to decreased costs associated with remediation efforts in the long run. By proactively addressing potential vulnerabilities during the development phase, developers can mitigate the risk of costly security breaches and data leaks, saving time and resources.
Overall, prioritizing security not only protects users but also benefits the developer or company by fostering a reputation for reliability and reducing the financial burden of security incidents.




