If you have a computer, you have a firewall. Most people don’t even know it’s there and never need to touch it. What matters is that firewalls work in the background to keep us safe. However, businesses must carefully choose firewalls, as they are their networks’ first defence against internal and external threats.
Let’s start understanding what firewalls are, their types, how they work, and their main features.
What is a network firewall?
 A firewall is a router that enforces security policies. This means it decides what traffic is allowed and denied on the network. For example, firewall policies can be applied to single users or groups of users to allow or deny their ability to reach specific websites, like social media, or to use particular applications. At the same time, firewall rules can determine what type of traffic can reach the users on the internal network from the Internet.
A firewall is a router that enforces security policies. This means it decides what traffic is allowed and denied on the network. For example, firewall policies can be applied to single users or groups of users to allow or deny their ability to reach specific websites, like social media, or to use particular applications. At the same time, firewall rules can determine what type of traffic can reach the users on the internal network from the Internet.
How do firewalls work?
Firewall policies are a set of rules applied together to cover real-life communication scenarios. Firewalls organize policies by Access Control Lists (ACLs) specifying which users or system processes are granted access to objects and what operations are allowed on those objects.
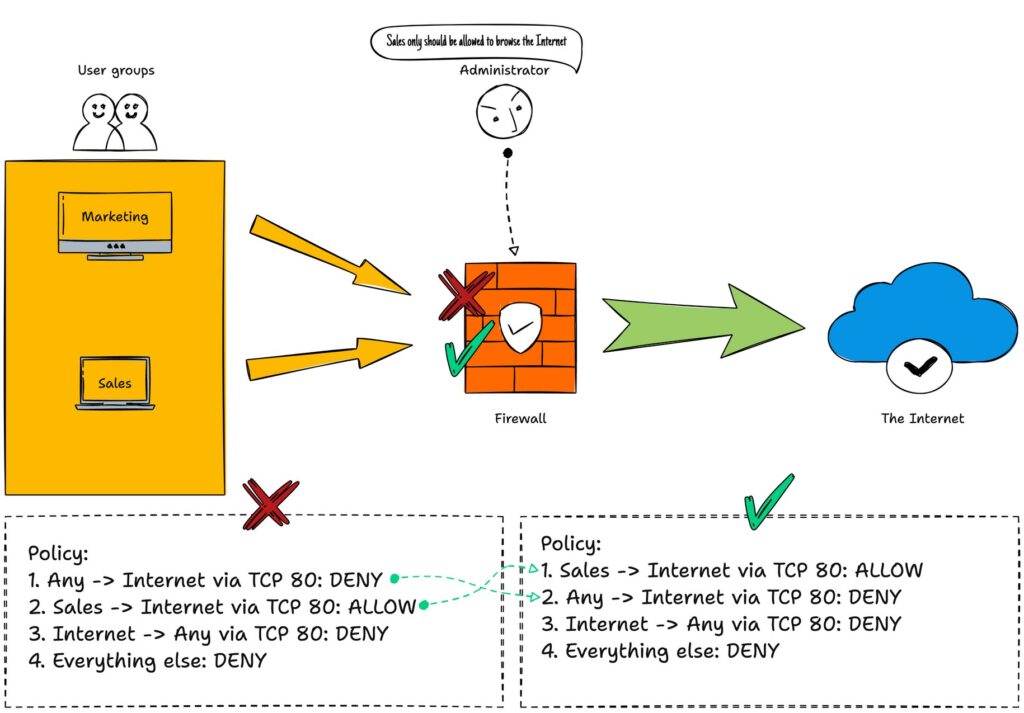
Firewall policies are evaluated against the packets in top-down order and on a first-mention basis. This is important when configuring the firewall so that the policy rules don’t interfere with each other and are applied in the intended way.
In the example below, the administrator intends to allow the sales department to browse the Internet. However, the first set of rules has been set in the wrong order: by blocking all traffic with the first rule, the second rule won’t be evaluated. To achieve the intended result, the first two rules must be swapped.
Another factor influencing how rules are applied in a firewall is the type of firewall we use. Indeed, Access Control Lists (ACLs) will be applied differently depending on whether the firewall is stateful or stateless.
Stateless firewalls
A stateless firewall operates with packet filters that do not adhere to protocols. This lack of protocol understanding can lead to significant issues, as each packet is treated individually.
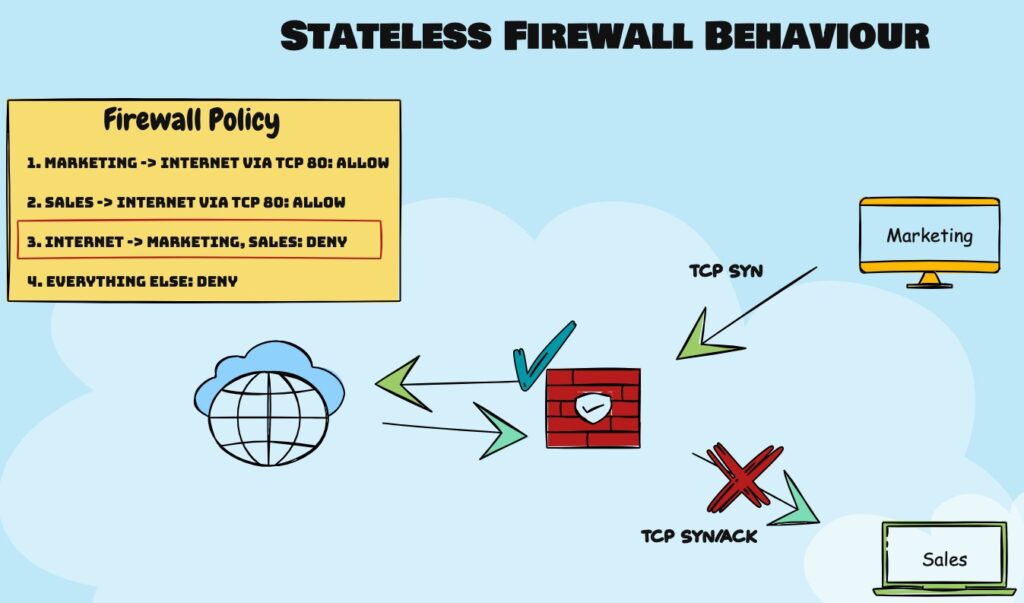
With the set of rules in this example, a stateless firewall would drop the TCP SYN handshake because rule #3 blocks communications from the Internet to both departments. To fix the problem, we must create an additional rule allowing communication from the Internet to Sales and Finance through port 80. However, this introduces a risk because anyone from the Internet can now generate packets to flood our firewall. This underscores the importance of selecting the appropriate firewall for your network’s security needs.
Stateful firewalls
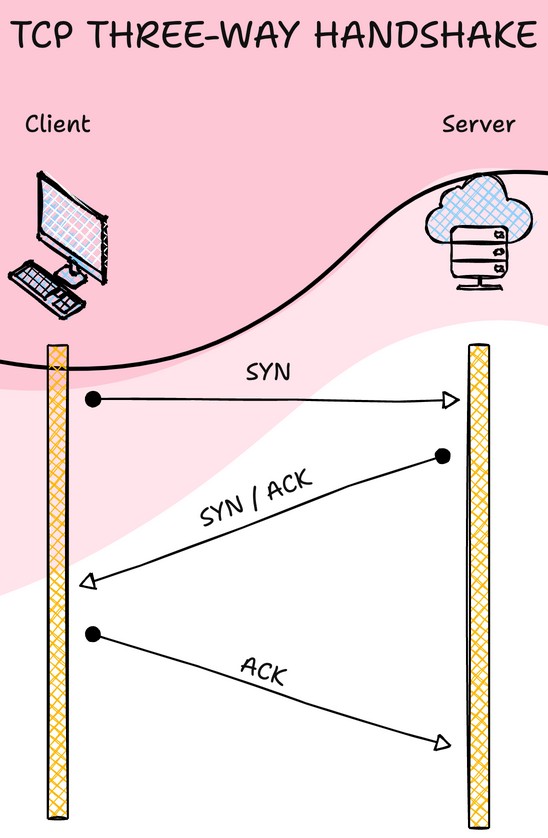 Stateful firewalls exhibit a profound comprehension of connection establishment across diverse protocols. They maintain connection tables that log vital information like source and destination addresses and ports, protocol type, and connection state. This knowledge allows the firewall to foresee the expected behaviour after each interaction and discard anything that strays from it. For instance, a stateful firewall promptly terminates a connection upon detecting a TCP FIN or TCP RST packet. The connection details are purged from the table, and only initial packets are permitted afterwards, ensuring a robust security posture.
Stateful firewalls exhibit a profound comprehension of connection establishment across diverse protocols. They maintain connection tables that log vital information like source and destination addresses and ports, protocol type, and connection state. This knowledge allows the firewall to foresee the expected behaviour after each interaction and discard anything that strays from it. For instance, a stateful firewall promptly terminates a connection upon detecting a TCP FIN or TCP RST packet. The connection details are purged from the table, and only initial packets are permitted afterwards, ensuring a robust security posture.
However sophisticated, stateful firewalls are not immune to issues:
- Attackers can still predict the TCP sequence numbers of the router’s table and the OS running on the application to bypass the firewall.
- Stateful firewalls have limitations when it comes to UDP communications. They can only log source and destination IPs and ports in their tables, lacking the ability to anticipate the course of communications. This underscores the need for alternative security measures in such scenarios.
- Other advanced features of stateful firewalls can sometimes backfire in specific scenarios. For instance, stateful firewalls incorporate an idle timer and a byte counter to thwart Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks. However, in poorly coded applications or those reliant on an idle or prolonged connection with a small number of packets (such as ODBC connections from databases), the firewall might drop these packets, leading to application issues. The idle timer can be adjusted in the firewall to mitigate these risks. However, it will need additional memory.
Stateless vs Stateful firewall summary
Here’s a recap of the advantages and disadvantages of stateless and stateful firewalls.
| Stateless firewalls | Stateful firewalls |
|---|---|
| Cannot recognize and allow server replies. | Can recognize and allow server replies. |
| Can be used if you trust the server-side of the connection. | Are more resource intensive and might cause issues with some applications. |
Points to consider when choosing a firewall
When choosing a firewall, you should focus on the following points:
- The amount of traffic that can pass through the firewall
- The amount of connections per second that the firewall can handle
- The amount of memory the firewall needs to keep the data in its tables.
 Many online tools allow you to “size” your firewall needs. However, firewall experts advise that the best way to evaluate whether a firewall is good for you is through a POC (Proof of Concept) on your production traffic. Many providers accept copies of your traffic over a period of time for evaluation: that’s a safe and non-disruptive way of having an expert opinion based on your real-life network usage.
Many online tools allow you to “size” your firewall needs. However, firewall experts advise that the best way to evaluate whether a firewall is good for you is through a POC (Proof of Concept) on your production traffic. Many providers accept copies of your traffic over a period of time for evaluation: that’s a safe and non-disruptive way of having an expert opinion based on your real-life network usage.
Next-Generation firewalls
Next-generation firewalls are stateful firewalls on steroids. They have advanced features such as anti-malware detection, intrusion detection and protection, decryption, and even user identity mapping (integration with identity management systems such as Active Directory).
Our next article will explore what they are, what they can do, and how to choose them based on your needs.




