Developers typically have one goal in mind: building functional, user-friendly applications. However, being a good coder only sometimes means that the application is well-built from a security perspective. Most of the time, security is an afterthought with last-minute modifications to comply with basic requirements.
There are so many threats to web applications that more than basic security is needed. Building secure apps must start from the design process. So here’s the first of a series of articles addressing all the critical points of building security into your web applications.
Web app vulnerabilities you should know about
The first step to building secure applications is understanding the threats. Session hijacking is one of the most common vulnerabilities of web-based applications. This includes a variety of attacks at different levels that aim to interject the user session and bypass the authentication process.
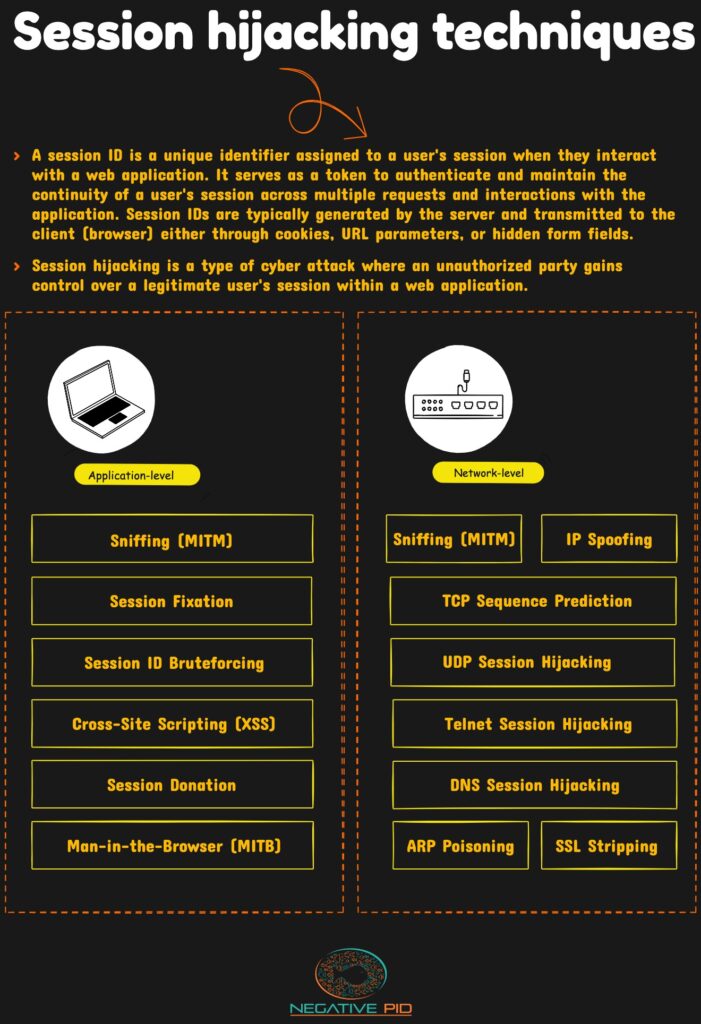
Application-level hijacking techniques
Session hijacking at the application level can take many shapes. Here’s an overview of the most popular techniques:
- Session sniffing is an MITM (Man-in-the-Middle) attack where the target is session data in transit.
- Session fixation involves the manipulation of session identifiers to gain unauthorized access.
- Session ID brute-forcing involves systematically guessing session IDs to breach authentication mechanisms.
- Cross-site scripting (XSS) vulnerabilities enable attackers to inject malicious scripts into web pages, compromising user data and session integrity.
- Session Donation attacks are a type of social engineering technique. In such cases, the malicious party shares a session ID with the user.
- Man-in-the-Browser (MITB) attacks involve leveraging compromised browser sessions to execute unauthorized actions.
An integrated approach to web app security
An integrated approach to web app security should take into consideration the following aspects:
- Robust session IDs
- URL security
- Prevention of Session ID reuse
- Cookie parameter optimization.

Best practices for generating robust Session ID's
 Creating complex and robust session IDs is the first step in hardening your application’s security. When choosing a token or ID generator, make sure that the created values follow these principles:
Creating complex and robust session IDs is the first step in hardening your application’s security. When choosing a token or ID generator, make sure that the created values follow these principles:
- Use unique session IDs: Treat session IDs as passwords; they should be unique to each session and highly sensitive.
- Use random IDs: Generate session IDs randomly to thwart predictability and enumeration attempts.
- Use alphanumeric combinations: Use alphanumeric combinations for session IDs instead of only numbers or letters.
- Use lengthy IDs: Ensure session IDs are lengthy enough to withstand brute force attacks, enhancing their resilience.
Best practices for URL security optimization
 Incorporating session IDs into URLs is a risky habit. This practice exposes the user session to several vulnerabilities and should be avoided. Indeed, session IDs embedded in URLs may surface in various endpoints, such as logs, web browser history, and bookmarks, widening the attack surface.
Incorporating session IDs into URLs is a risky habit. This practice exposes the user session to several vulnerabilities and should be avoided. Indeed, session IDs embedded in URLs may surface in various endpoints, such as logs, web browser history, and bookmarks, widening the attack surface.
Instead, you can:
PREFER POST OVER GET
Employ the POST method when transmitting sensitive session data instead of GET. This is because:
| GET REQUESTS | POST REQUESTS |
|---|---|
| GET requests are more prone to being cached by browsers, proxy servers, and other intermediaries, potentially exposing sensitive data in cached copies. | POST requests transmit data within the request body rather than appending it to the URL lile GET requests. This means that sensitive session data is not exposed in the URL. |
| GET requests are more likely to be logged in various places such as server logs, browser history, or proxies. | POST requests can accommodate larger volumes of data, allowing for the secure transmission of extensive session-related information. |
Ultimately, employing POST requests helps mitigate these risks by minimizing the exposure of sensitive data in logs and caches.
LEVERAGE COOKIES
Use cookies wherever feasible for session management. There are several advantages to leveraging cookies for session management:
- Security attributes: Cookies can be configured with attributes such as HttpOnly and Secure.
- HttpOnly prevents client-side scripts from accessing the cookie, reducing the risk of cross-site scripting (XSS) attacks.
- Secure ensures that cookies are only transmitted over encrypted HTTPS connections, mitigating the risk of interception and unauthorized access.
- Simplification: Cookies are automatically included in HTTP requests by the browser, simplifying session management for developers. Once set, cookies persist across multiple requests without requiring manual handling or appending URL session IDs.
- Flexibility: Cookies offer more flexibility in managing session data compared to URLs. Developers can store various session attributes and metadata within cookies, facilitating more sophisticated session management functionalities.
- Storage security: Unlike URLs, which may be exposed in various places such as browser history, referrer headers, and logs, cookies are typically stored securely on the client side and transmitted only to the originating server. This reduces the risk of unintentional session data exposure.
- Scalability: Using cookies for session management can improve web applications’ scalability by reducing URL size.
Best practices for preventing session ID reuse
 Re-using the same session ID is a practice that undermines the security of user sessions. Indeed, it increases the risk of session fixation, introduces predictability, and compromises session isolation. Developers must generate unique session IDs for each session to mitigate these security risks effectively. To do that, follow these precautions:
Re-using the same session ID is a practice that undermines the security of user sessions. Indeed, it increases the risk of session fixation, introduces predictability, and compromises session isolation. Developers must generate unique session IDs for each session to mitigate these security risks effectively. To do that, follow these precautions:
- Use fresh session IDs: Generate new session IDs post-authentication to circumvent session fixation attacks effectively.
- Exclude PIIs: To safeguard user privacy effectively, avoid incorporating personally identifiable information (PII) into your session IDs.
Best practices to optimize cookie parameters
 Cookie parameters are attributes that help manage sessions in web applications. These parameters dictate how cookies behave and are transmitted between the client (browser) and the server.
Cookie parameters are attributes that help manage sessions in web applications. These parameters dictate how cookies behave and are transmitted between the client (browser) and the server.
Fine-tuning cookie parameters is a strategy that can greatly enhance session management security:
- Use HTTP Only: Employ the HTTP Only attribute to restrict script access, ensuring that session data remains inaccessible to client-side scripts.
- Use Secure: Enforce the Secure attribute to confine cookie transmission exclusively to encrypted HTTPS connections, thwarting potential eavesdropping attempts.
- Set expiration parameters: Implement the MAX-AGE or EXPIRE attribute to regulate session longevity, mitigating the risk of prolonged exposure to potential threats.
- Use SAMESITE and DOMAIN: Tailor the SAMESITE and DOMAIN parameters based on implementation specifics to delineate which sites possess cookie access.
Building web apps that plan for preventing application-level threats is a great first step toward web app security. However, it’s not enough. An integrated approach should also take into consideration network-level session security and overall security design.
In our next article, we’ll cover how to achieve that.




