Have you ever tried googling yourself? The amount of information you can find online just by inserting your name into a search engine can be surprising. Now imagine the amount of information someone skilled could find without “just browsing.” It is estimated that only 4% of the available information online resides on the Internet. The rest is scattered in the deep web (made of databases and repositories) and the dark web. The professional information-gathering process requires knowledge, tools, and skills. The framework that gathers it all into a science is called Open Source Intelligence (OSINT).
What is OSINT?
 Intelligence can be defined as any organized set of data (information) useful for decision-making. It enables decision-makers to make informed decisions based on data and context, thus reducing the risk of failure. Intelligence actors pass on (or disseminate) intelligence to their customers in a format they can use to make decisions.
Intelligence can be defined as any organized set of data (information) useful for decision-making. It enables decision-makers to make informed decisions based on data and context, thus reducing the risk of failure. Intelligence actors pass on (or disseminate) intelligence to their customers in a format they can use to make decisions.
More often than not, this information is collected by public sources, meaning that it’s already out there, somewhere, and is accessible (thus making it open source). OSINT is a framework for the collection, exploitation, and dissemination of publicly available information promptly to an appropriate audience to address a specific intelligence requirement.
OSINT is also a continuous process of gathering, analyzing, sharing, and getting feedback about some subject.
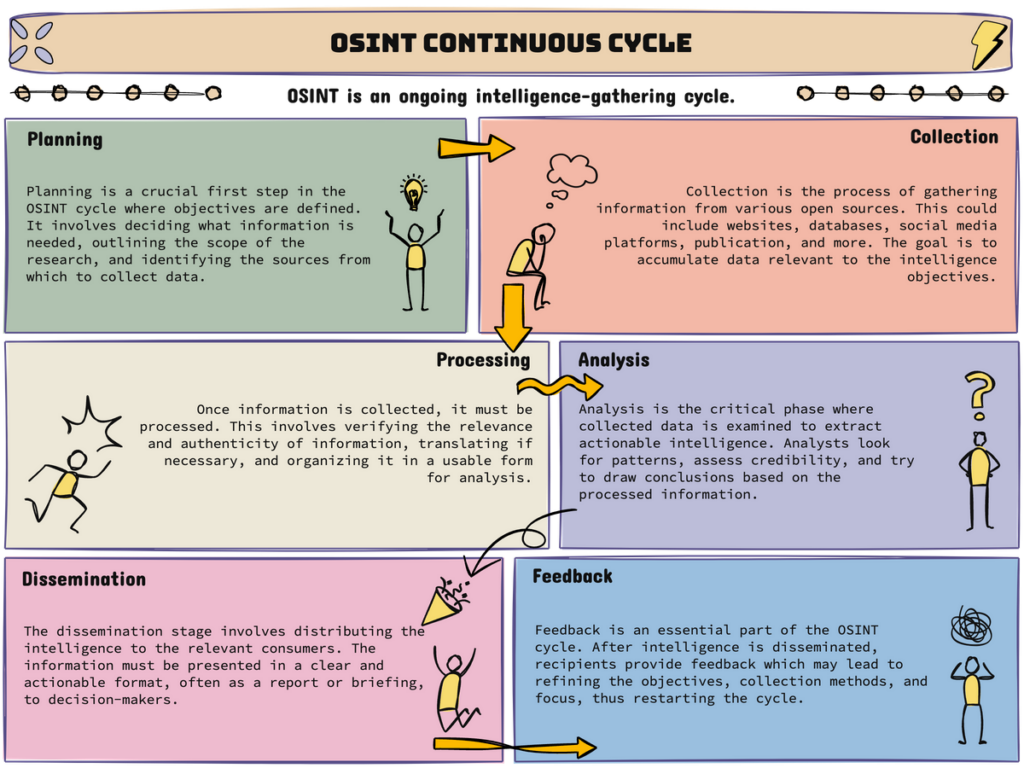
Who uses OSINT?
The simple answer is that every person who uses a search engine uses OSINT to some degree. Anybody researching a subject uses—knowingly or not—some OSINT technique, from teachers and parents to company employees, for marketing, sales, or HR purposes.
However, some people, such as private investigators, law enforcement, the Military, and IT people, use OSINT more extensively and purposely for offensive or defensive purposes.
Indeed, more than 70% of pen-testing work (i.e., finding vulnerabilities in computer systems for defensive purposes) consists of reconnaissance with OSINT techniques.
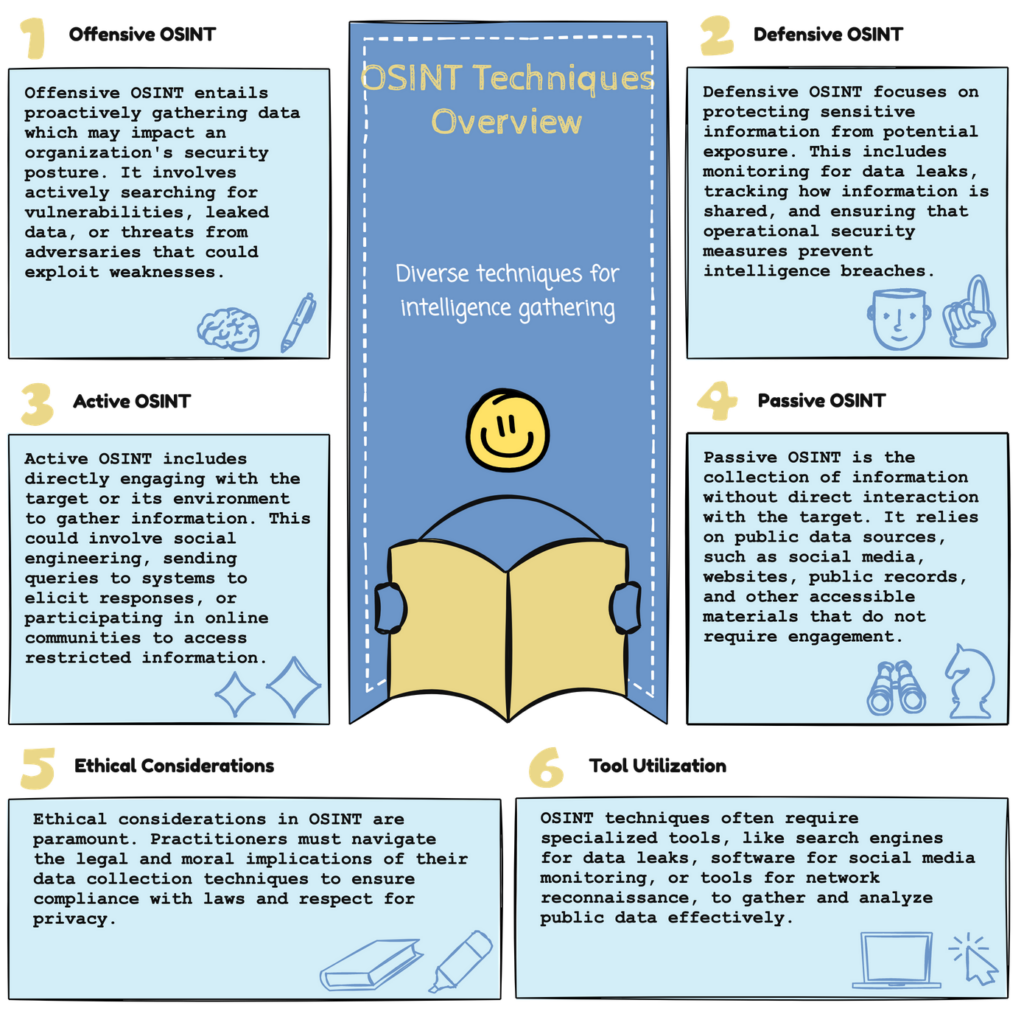
Types of OSINT techniques
OSINT techniques can be used for defensive or offensive purposes. While finding the information is part of the investigation process, in many cases, the ethical dilemma consists of whether to access the discovered information and what to do with it. Often, investigators walk a fine line between ethical and unethical, and lawyers are a good resource for determining an investigator’s actions.
OSINT techniques can also be categorized as active or passive. Active OSINT is typically used to learn the digital footprint of a target individual or organization. Active OSINT typically leaves a trace behind, for example, when using a port scanner, we send a probe to the target system that might be detected. Passive OSINT conducts invisible investigations with no active contact with the target, for example, when doing a search on a search engine.
Is OSINT a threat?
 OSINT comes with some implicit threats: hacking, social engineering, phishing, malware, data and information breaches and leaks all take advantage of the OSINT framework. Misinformation (people spreading information they believe is true) and disinformation (sharing false information to mislead others) are also issues in the data-gathering process.
OSINT comes with some implicit threats: hacking, social engineering, phishing, malware, data and information breaches and leaks all take advantage of the OSINT framework. Misinformation (people spreading information they believe is true) and disinformation (sharing false information to mislead others) are also issues in the data-gathering process.
PROTECTIVE MEASURES
In the same way that you wouldn’t hand over the keys to your house to anybody, you can defend yourself by simply maintaining good digital security habits such as:
- Educating yourself on cybersecurity threats and phishing
- Maintaining online privacy hygiene (such as not oversharing on social media, adopting a secure browser with security browser extensions, using VPNs and antivirus)
- Hardening your IT system security
- Adopting a solid password and using offline password managers
- Monitoring breaches (an intentional release of secure or private information) and leaks (the accidental release of secure or private information) to check if your credentials are now public.
At Negative PID, we use OSINT for our Intelligence and InfoSec services. Have a look at our website to see what we can do for you!




